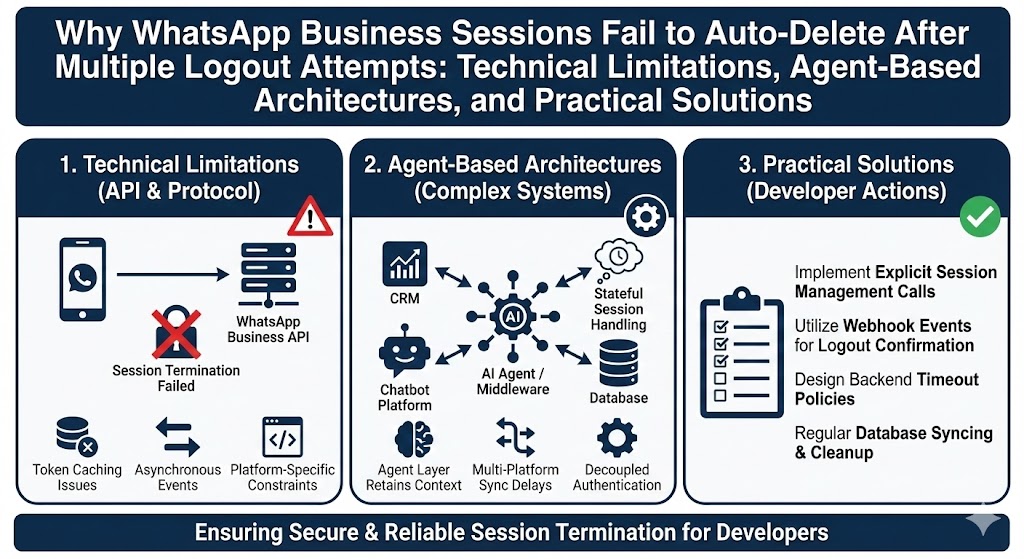
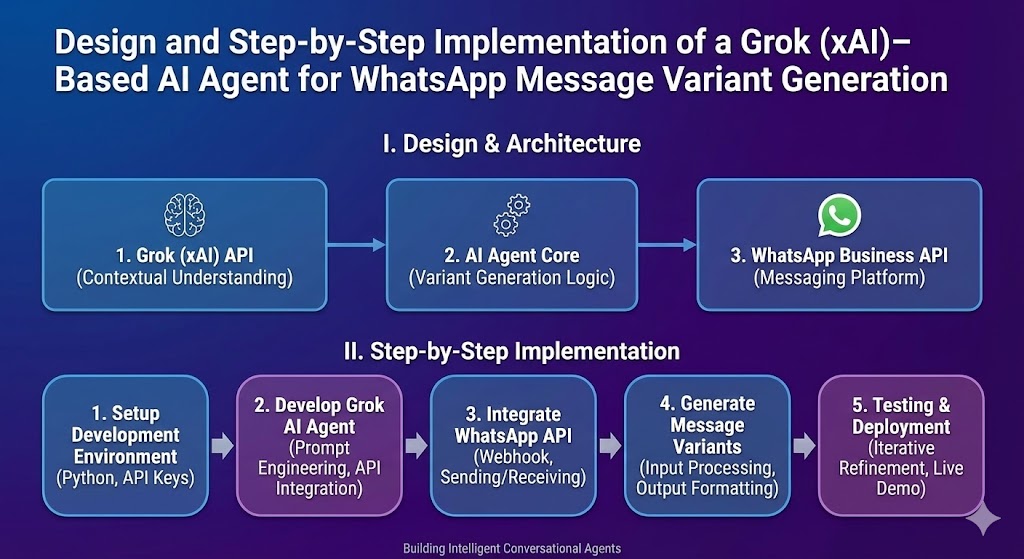
Apologies for the oversight. Let’s continue with a more comprehensive approach to cover all outlined headings in the article on future cybersecurity risks:
Future Cybersecurity Risks: An Analytical Insight
In an interconnected world driven by digital innovation, cybersecurity stands as a critical pillar safeguarding businesses, governments, and individuals from evolving threats. This article explores the complex landscape of future cybersecurity risks through an analytical lens, supported by data, case studies, and expert insights.
The Escalating Cost of Cybercrime
Cybercrime has evolved into a multi-trillion-dollar industry with profound economic implications. By 2025, global cybercrime costs are projected to escalate to $10.5 trillion annually, reflecting a significant rise from $3 trillion in 2015. This exponential increase is fueled by several factors driving the cost of cybercrime:
Factors Driving Cost Increase:
- Sophistication of Attacks: Cybercriminals deploy sophisticated tactics such as Advanced Persistent Threats (APTs) and ransomware to infiltrate systems and compromise data. These attacks are designed to evade traditional cybersecurity measures, leading to prolonged breaches and substantial financial losses.
- Economic Impact: Major cyber incidents, such as the SolarWinds supply chain attack and the Colonial Pipeline ransomware attack, have demonstrated the severe economic impact of cyber threats. These incidents disrupt operations, damage reputation, and incur significant financial costs, affecting industries ranging from healthcare to finance.
- Global Connectivity: The interconnected nature of digital ecosystems and global supply chains expands the attack surface for cybercriminals. This interconnectedness facilitates the rapid propagation of cyber threats across borders, amplifying their impact on international business operations and critical infrastructure.
Advanced Persistent Threats (APTs): Strategic and Stealthy
APTs pose a persistent threat to governments and enterprises worldwide, characterized by their stealthy infiltration and long-term presence within compromised networks. These sophisticated cyberattacks are often state-sponsored and target sensitive information for espionage or sabotage purposes.
Case Studies and Examples:
- SolarWinds Attack: In 2020, the SolarWinds supply chain attack compromised multiple U.S. government agencies and private companies by exploiting vulnerabilities in software updates. This orchestrated cyber espionage campaign went undetected for months, underscoring vulnerabilities in supply chain security and the sophistication of APT tactics.
- NotPetya Ransomware: The NotPetya ransomware attack in 2017 originated in Ukraine but quickly spread globally, affecting multinational corporations and causing billions of dollars in damages. This incident highlighted the interconnected nature of cyber threats and their potential to disrupt global business operations on a massive scale.
Ransomware: Evolution and Economic Disruption
Ransomware attacks continue to evolve in complexity and impact, posing significant risks to organizations across sectors. These attacks encrypt critical data and demand ransom payments in exchange for decryption keys, often with threats of data exposure or permanent loss.
Financial and Operational Impacts:
- SonicWall’s Cyber Threat Report indicates a 105% increase in ransomware attacks in 2021 compared to the previous year, highlighting the growing frequency and severity of ransomware incidents.
- The Colonial Pipeline ransomware attack in 2021 disrupted fuel supply chains across the U.S. East Coast, leading to fuel shortages, operational shutdowns, and substantial financial losses. This incident underscored vulnerabilities in critical infrastructure and the systemic risks posed by cyber disruptions.
Internet of Things (IoT) Vulnerabilities: Expanding Attack Surfaces
The proliferation of Internet of Things (IoT) devices introduces new cybersecurity challenges, as these connected devices often lack robust security measures. With an estimated 25 billion IoT devices projected by 2025, the expansion of attack surfaces increases the vulnerability to cyber exploits and compromises sensitive data.
Security Challenges and Mitigation Strategies:
- Vulnerabilities in IoT devices were exploited in the Mirai botnet attack in 2016, which utilized compromised devices to orchestrate massive distributed denial-of-service (DDoS) attacks. This incident highlighted the critical need for standardized security protocols and proactive measures to secure IoT ecosystems.

Artificial Intelligence (AI) and Machine Learning (ML) in Cybersecurity: Opportunities and Risks
AI and ML technologies offer promising capabilities for enhancing cybersecurity defenses, including threat detection and anomaly recognition. However, these technologies also present new risks, as cybercriminals leverage AI-driven tactics to orchestrate sophisticated attacks and evade detection.
Benefits and Risks of AI/ML:
- AI-powered phishing attacks can mimic human behavior and generate convincing social engineering tactics, posing challenges for traditional cybersecurity defenses.
- As AI and ML adoption accelerates, organizations must prioritize cybersecurity investments in AI-driven threat intelligence and adaptive security measures to effectively combat evolving cyber threats.
Conclusion: Navigating Future Cybersecurity Challenges
The future of cybersecurity demands proactive strategies, collaboration across sectors, and continuous innovation to mitigate risks effectively. By investing in robust cybersecurity frameworks, enhancing threat intelligence capabilities, and fostering a culture of cybersecurity awareness, organizations can strengthen resilience against emerging threats and safeguard digital assets in an increasingly interconnected world.